GIAG 2021 Web 1 Challenge Guide
Ben Silverman - October 13, 2021
This guide is for the Web 1 challenge of our 2021 Give It A Go workshop!
You can find the challenge here in case you'd like to attempt it first before reading the rest of this page.
The challenge
This challenge presents us with the following content:
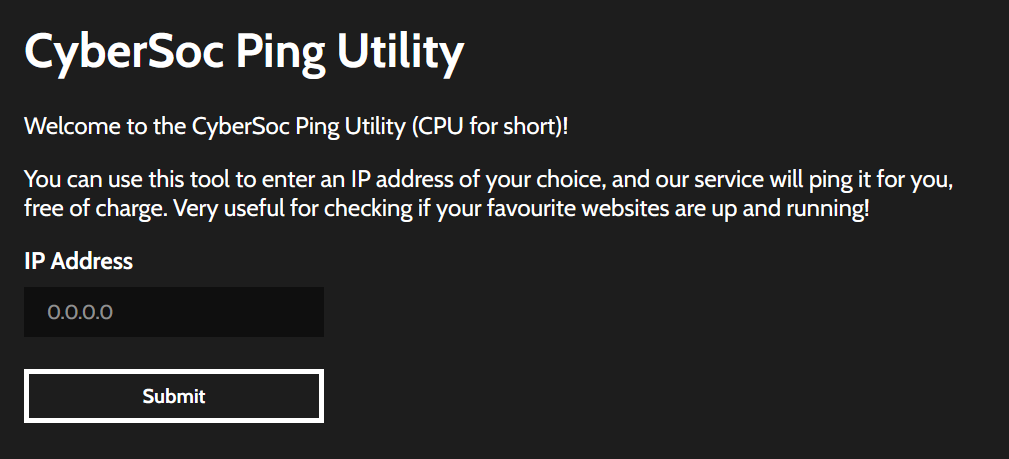
We can enter an IP address into the input field, and the utility will return a reponse containing how long it took to pin the address. Pretty straightforward! We're going to need to find some kind of key in this
Hint #1
Click here to reveal.
Think about how the utility might be running in the backend.
How would you going about pinging an IP address if you wanted to?
Hint #2
Click here to reveal.
You can chain Linux commands together with operators like && and ||
How could that be used in this context?
Hint #3
Click here to reveal.
The command the server is running essentially looks like this:
exec("ping [your input here]")
How can you take advantage of this?
Full Walkthrough
If you've used the hints above and are still at a bit of a loss, don't worry! We've written a full walkthrough of the challenge so you can still complete it and learn something new. Hopefully we'll do something like this again another time and you'll be able to use this new knowledge to your advantage!
Click here to reveal.
As shown in Hint #3, the server runs something called an exec() command to ping the IP address we provide. This creates a shell on the server, executes the command, and sends the result of that command back to the server, where it then gets sent back to us in the browser.
The way we can take advantage of this is by including something other than an IP address in that input field; it'll get passed through to the shell and run just like any other command would.
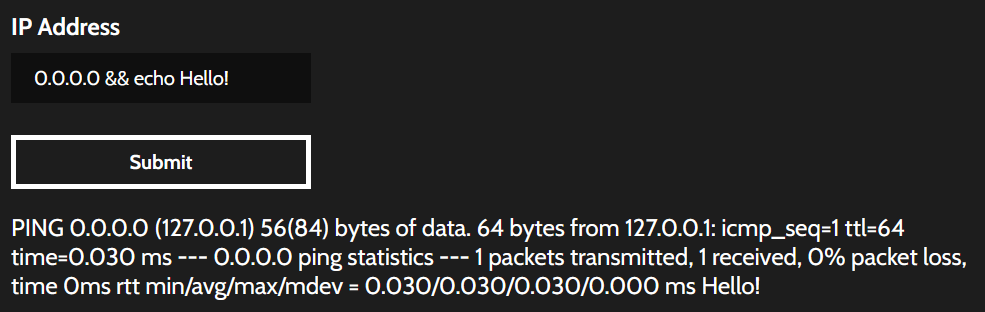
Like Hint #2 says, if we provide an IP address as the first part of our input but then chain another command onto the end, we can get the server to run it and return even more stuff than it's supposed to. Try using the code below as you input:
0.0.0.0 && echo Hello!
You should see something else appear at the end of the response:
This might be enough help for you to carry on by yourself, now, so feel free if that's the case!
Continuing on, though, we can see that it's possible to get the server to run commands of our choosing. Very powerful indeed!
To list the files in the same directory as the server, you can use 0.0.0.0 && ls as your input. See how they get added to the end of the response?
After doing that, you might notice a key.txt sitting there. How about we try and cat that and see what it says?
Enter 0.0.0.0 && cat key.txt and we're done. Well done on finding the key! 😄
Hopefully this walkthrough helped in explaining how the attack we just did worked. If you still would like a little more help, grab one of our committee members and they'll be sure to explain anything else they can.